DATA SECURITY PROCESS
Effective measures for data and information security are sine qua non of a reliable and unwavering outsourcing partner. Aware of client concerns for data breaches and misuses, Aidedo offers to make assured data and information security an integral component of outsourcing contracts to generate client confidence.
Our stringent security policies are fully compliant to project information criticality, pace, and scale of outsourcing aimed at improving vendor-client collaboration, mutual trust, and ethical business practices. We use a variety of technologies, data formats, and measures that eliminate the risk of information breaches, secure data from becoming privy to unintended recipients, and allow full control and use of data only for specified purpose.

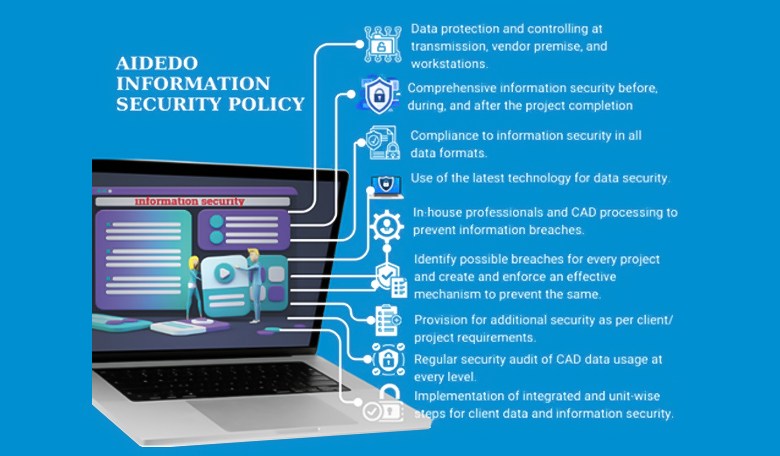
Aidedo Information Security Policy: Key Features
- Data protection and controlling at transmission, vendor premise, and workstations.
- Comprehensive information security before, during, and after the project completion
- Compliance to information security in all data formats.
- Use of the latest technology for data security.
- In-house professionals and CAD processing to prevent information breaches.
- Identify possible breaches for every project and create and enforce an effective mechanism to prevent the same.
- Provision for additional security as per client/ project requirements.
- Regular security audit of CAD data usage at every level.
- Implementation of integrated and unit-wise steps for client data and information security.
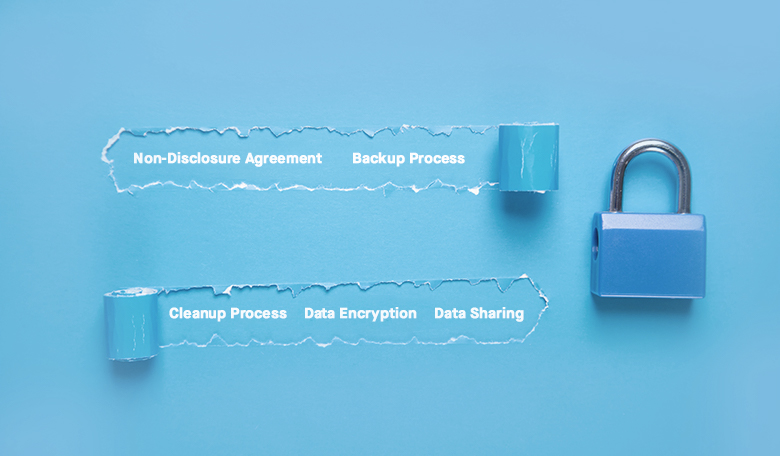
Data Security Safeguards at Aidedo
We have strict security practices at a number of levels to counter CAD data security breaches. These are as follow:
- Non-Disclosure Agreement: Aidedo is ready to sign Non-Disclosure Agreement with clients as and when they ask for. This testifies our willingness to convert the data security commitment into a legal binding instrument guaranteeing top-level information security practices. Our professional employees are bound by NDA terms and security practices explicitly mentioned in their employment terms.
- Backup Process: We backup the files regularly and keep them in secure zones with restricted access. All data on the main drive is deleted on the daily basis.
- Cleanup Process: We do not backup data for project completed without explicit client request. The data was either destroyed or returned back.
- Data Encryption: Encrypted email, folders, and files assure data confidentiality and eliminate the risk of braches during the sharing process.
- Data Sharing: Only authorized employees are allowed to share data and that too within set information security guidelines. Aidedo does not allow sharing of source files.

Data Leak Prevention System
At Aidedo, we have a Data Leak Prevention System to:
Monitoring access to all sensitive files and recording granular usage data such as user, department, file accessed, file type and operation response time.
Alerting on, and automatically blocking, file actions that violate security policies.
Detecting abnormal or suspicious user behavior using software that runs silently, to detect insider threats.
Mitigating Ransomware attacks by detecting and blocking typical file access patterns.
Auditing and reporting on all file operations for compliance and investigation purposes.
Also, we shred all printed drawings after we perform the QC process.
Aidedo Employee Access Control
We restrict information inflow at various individual employee levels that prevent unauthorized access, data misuse, and information breaches. These include the following measures.
Protected system access only for employees working on the project
Network logins protected by password
No remote access is allowed
All emails and files are encrypted with mandatory digital signatures
Single sign-in and password protected systems and enterprise applications
24-hour security surveillance and advanced technology for monitoring
Separate security and administrative monitoring
USB ports, CD, and other storage devices are not allowed
Regular system auditing
Latest anti-virus programs for every work station
Centralized backup management